In November, the Integritee team kept working on Incognitee to launch new exciting features. We’ve been receiving great feedback on the usage rate of Incognitee, the TEERdays campaign, and the Guess the Number contest. Keep scrolling to find out what we were up to last month!
Business Updates
Incognitee on Integritee Network Stats
Incognitee is in full steam and in November, we witnessed 1149 events generated by users, including private balance transfers, Guess the Number interactions, and others. Here are last month’s event numbers:
- Private balance transfers: 101
- Guess the Number events: 972
- Shieldings: 66
- Unshieldings: 10
- The current TVL on L2 is 18,101 TEER.
The Incognitee Polkadot launch is around the corner and will accelerate the usage significantly. Try Incognitee now.
Incognitee listed on the Dapp Browser of Subwallet and Novawallet
Incognitee is now available via quick access through the dApp browser of Subwallet and Novawallet. Just go to the browser section of the wallet, type in Inc… or scroll down to Incognitee and connect your wallet easily for use with Incognitee.
Guess the Number Contest Stats
Last month, four weekly contests were conducted, and 2,000 TEER were distributed among the winners.
We had a total of 972 guesses and three different winners. Feeling lucky today? Take a minute to place a guess and win 500 TEER.
Want to enter the contest, but don’t know how it works? No worries, we’ve got you covered! Our team published a short video tutorial explaining how to enter the contest and how to transfer TEER on Incognitee.
Progression of the TEERdays
The TEERdays campaign continues to attract enthusiasts wanting to participate in the success of Incognitee, and the numbers are looking good: by the end of November, we had surpassed 70 million active TEERdays, more than 1,360,000 TEER bonded by 77 TEERday holders. Bond your TEER today as well and earn TEERdays.
November Content
The Evolution of Smart Contracts: What’s Next?
Smart contracts and the underlying technology have been heavily used across different industries, from healthcare to logistics, finance to humanitarian aid. This November, our content team wrote an article on what’s next for smart contracts, and how will tools such as AI and layered solutions be incorporated to enhance this technology’s reach. Read it here.
Blockchain and Cybersecurity: Can Decentralization Solve the Biggest Security Challenges?
Has blockchain come to the cybersecurity industry’s rescue? That’s what we decided to explore in the article “Blockchain and Cybersecurity: Can Decentralization Solve the Biggest Security Challenges?”. We delved into how this technology, when combined with others, is able to provide more security and protection on transactions and other digital tasks. However, we might still be a few steps behind on cybersecurity solutions that are 100% blockchain-based. Check out our article here.
Community Update
In episode 22 of “It’s TEE Time!”, Waldemar Scherer and Sergei Medvedev shared a few updates regarding Incognitee, the TEERdays campaign, and what the tech team has been working on. They also answered some questions from our community. Listen to the full recording here.
Web3 Global AMA
Last month, we participated in yet another talk hosted by Web3 Global, together with other Web3 projects. It was an insightful conversation where matters like the state of the crypto industry, politics, freedom, and democracy intersected. You can listen to the full episode here.
Governance
Referendum #38: Register KSM asset on Integritee Network
This referendum ended with 100% Aye votes. The Integritee council proposed to Register KSM as an asset on Integritee Network. Check out more details.
Referendum #39: Register TEER token metadata on Asset Hub
This referendum ended with 100% Aye votes. The Integritee council proposed to Register TEER token metadata on Asset Hub. Know more about it.
Referendum #40: Register KSM asset on Integritee Network (2nd try)
Because of a technical issue with the enactment of referendum #38, we had to rerun it. This referendum ended with 100% Aye votes. The Integritee council proposed to Register KSM as an asset on Integritee Network, and this is where you can find more information on the vote.
Referendum #41: Update Incognitee Sidechain Enclave to 0.15.3
This referendum ended with 100% Aye votes. The Integritee council proposed to update the Incognitee Sidechain Enclave to 0.15.3. Read more about it.
Tech Updates
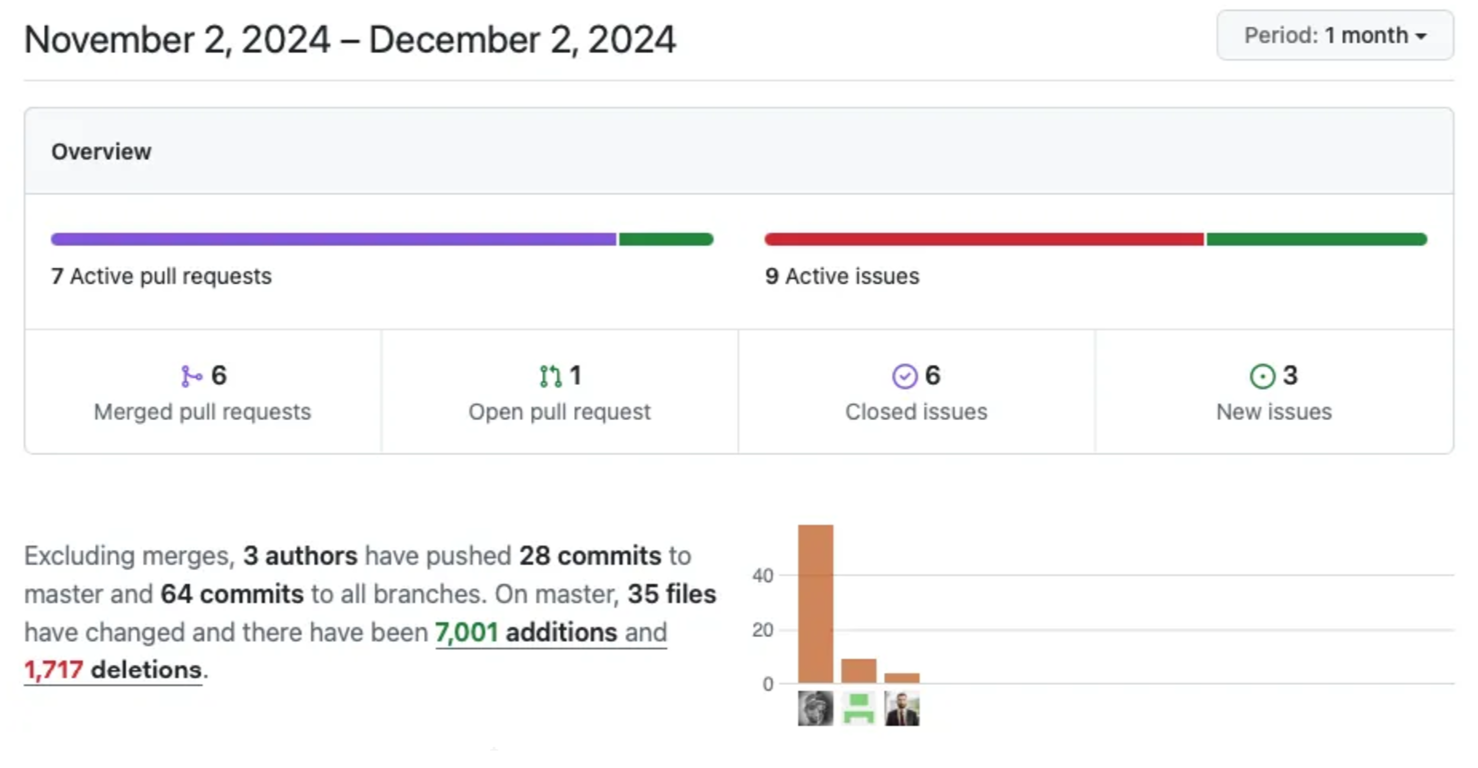
Technical advancements:
Integritee Parachain & SDK
- Release of SDK Versions v0.15.1, v0.15.2, and v0.15.3
- Charge byte fees for notes
- Change nonce init to respect xt in tx pool
- Add note bloat and waste time TrustedCalls and cli
- Store ringbuffer with notes in sgx_runtime
- Update nonce via rpc before producing a new sidechain block
- Make enclave extrinsics mortal
- Shutdown upon parentchain code update
- Return total issuance metric as decimal value
- More RPC methods
- Maintenance scripts
- Auto-restart if the init extrinsics fail
- Trusted call short-term memory for tracing
- Enclave extrinsic sent with invalid mortality checkpoint
- [Incognitee][prod] Many failed extrinsics for sidechain block confirmation
- Configurable enclave extrinsic mortality
- Shut down worker service gracefully whenever any parentchain dispatches System.CodeUpdated event
- [rpc] Lazy static Sidechain HEAD Header
- An error is reported when starting integritee-servic
- Extrinsic sender should keep track of spec version
Incognitee App
- Implement vouchers with design from #86
- Bug Fixes and UI Improvements for msg
- Ap/msg redesign
- Modularize pages to components and introduce messaging app
- Private tx history with optional notes
- Delete assets/.DS_Store
- Make some functions async and await calls
- Use the native websocket provided by @polkadot/rpc-provider
- Changing the account is tedious because the account change popup is closed upon a balance update
- Account Info getter is stuck sometimes
- Unshield default recipient account uses the substrate default ss58 prefix instead of the integritee prefix
- Confusing “how would you like to connect”
- Block actions if status is not green
- Limit unshielding amount
For more details, check our repository.
What’s Ahead
Incognitee: Next Steps
Incognitee is now live in beta production state, but what’s next? We are continuously working on the reliability and will monitor the behavior over the next couple of weeks. In the meantime, we will launch new user campaigns and features to test things out and engage with our community.
Launch of a Referral Campaign
We are currently preparing a referral campaign to boost the TEERdays campaign and spread the word beyond our own community.
Tech updates
More features around our Attesteer, our Teeracle, and the privacy Sidechains will be released in the upcoming weeks.
• • •
About Integritee
Integritee is the most scalable, privacy-enabling network with a Parachain on Kusama and Polkadot. Our SDK solution combines the security and trust of Polkadot, the scalability of second-layer Sidechains, and the confidentiality of Trusted Execution Environments (TEE), special-purpose hardware based on Intel Software Guard Extensions (SGX) technology inside which computations run securely, confidentially, and verifiably.
Community & Social Media:
Join Integritee on Discord | Telegram | Twitter | Medium | Youtube | LinkedIn | Website
Products:
L2 Sidechains | Trusted Off-chain Workers | Teeracle | Attesteer | Securitee | Incognitee
Integritee Network:
Governance | Explorer | Mainnet | Github
